#Network Encryption Trends
Explore tagged Tumblr posts
Text
Network Encryption Share | Segmented by Top Manufacturers & Geography Regions

Network Encryption Market Information
The Network Encryption Market Report provides essential insights for business strategists, offering a comprehensive overview of industry trends and growth projections. It includes detailed historical and future data on costs, revenues, supply, and demand, where applicable. The report features an in-depth analysis of the value chain and distributor networks.
Employing various analytical techniques such as SWOT analysis, Porter’s Five Forces analysis, and feasibility studies, the report offers a thorough understanding of competitive dynamics, the risk of substitutes and new entrants, and identifies strengths, challenges, and business opportunities. This detailed assessment covers current patterns, driving factors, limitations, emerging developments, and high-growth areas, aiding stakeholders in making informed strategic decisions based on both current and future market trends. Additionally, the report includes an examination of the Automatic Rising Arm Barriers sector and its key opportunities.
According to Straits Research, the global Network Encryption market size was valued at USD 4 Billion in 2021. It is projected to reach from USD XX Billion in 2022 to USD 8 Billion by 2030, growing at a CAGR of 9% during the forecast period (2022–2030).
Get Free Request Sample Report @ https://straitsresearch.com/report/network-encryption-market/request-sample
TOP Key Industry Players of the Network Encryption Market
Thales Trusted Cyber Technologies
ATMedia Gmbh
Atos SE
Juniper Networks Inc.
Certes Networks Inc.
Senetas Corporation Ltd
Viasat Inc.
Raytheon Technologies Corporation
Securosys SA
Packetlight Networks
Rohde & Schwarz Cybersecurity GmbH
Global Network Encryption Market: Segmentation
As a result of the Network Encryption market segmentation, the market is divided into sub-segments based on product type, application, as well as regional and country-level forecasts.
By Solution
Network Encryption Platforms
On-Premise
Cloud-based
Network Encryption Devices
Services
Professional Services
Security Consulting
Training & Education
Support & Maintenance
Managed Services
By Deployment Type
Cloud
On-premises
By Component
Hardware
Solutions and Services
By Organization Size
Small and Medium-sized Enterprises
Large-sized Enterprises
By End-User Industry
Telecom and IT
BFSI
Government
Media and Entertainment
Healthcare
Retail & E-Commerce
Other End-user Industries
Browse Full Report and TOC @ https://straitsresearch.com/report/network-encryption-market/request-sample
Reasons for Buying This Report:
Provides an analysis of the evolving competitive landscape of the Automatic Rising Arm Barriers market.
Offers analytical insights and strategic planning guidance to support informed business decisions.
Highlights key market dynamics, including drivers, restraints, emerging trends, developments, and opportunities.
Includes market estimates by region and profiles of various industry stakeholders.
Aids in understanding critical market segments.
Delivers extensive data on trends that could impact market growth.
Research Methodology:
Utilizes a robust methodology involving data triangulation with top-down and bottom-up approaches.
Validates market estimates through primary research with key stakeholders.
Estimates market size and forecasts for different segments at global, regional, and country levels using reliable published sources and stakeholder interviews.
About Straits Research
Straits Research is dedicated to providing businesses with the highest quality market research services. With a team of experienced researchers and analysts, we strive to deliver insightful and actionable data that helps our clients make informed decisions about their industry and market. Our customized approach allows us to tailor our research to each client's specific needs and goals, ensuring that they receive the most relevant and valuable insights.
Contact Us
Email: [email protected]
Address: 825 3rd Avenue, New York, NY, USA, 10022
Tel: UK: +44 203 695 0070, USA: +1 646 905 0080
#Network Encryption#Network Encryption Industry#Network Encryption Share#Network Encryption Size#Network Encryption Trends#Network Encryption Regional Analysis#Network Encryption Growth Rate
0 notes
Text
#Network Encryption Market#Network Encryption Market size#Network Encryption Market share#Network Encryption Market trends#Network Encryption Market analysis#Network Encryption Market forecast
0 notes
Text
Neo-Nazis and white supremacists are sharing Hitler-related propaganda and trying to recruit new members on TikTok, according to a new report from the Institute for Strategic Dialogue (ISD) shared exclusively with WIRED. The TikTok algorithm is also promoting this content to new users, researchers found, as extremist communities are leveraging the huge popularity of TikTok among younger audiences to spread their message.
The report from ISD details how hundreds of extremist TikTok accounts are openly posting videos promoting Holocaust denial and the glorification of Hitler and Nazi-era Germany, and suggesting that Nazi ideology is a solution to modern-day issues such as the alleged migrant invasion of Western countries. The accounts also show support for white supremacist mass shooters and livestream-related footage or recreations of these massacres. Many of the accounts use Nazi symbols in their profile pictures or include white supremacist codes in their usernames.
Nathan Doctor, an ISD researcher who authored the report, says he began his investigation earlier this year when he came across one neo-Nazi account on TikTok while conducting research for another project.
He was quickly able to unmask a much broader network of accounts that appeared to be actively helping each other through liking, sharing, and commenting on each other’s accounts in order to increase their viewership and reach.
The groups promoting neo-Nazi narratives are typically siloed in more fringe platforms, like Telegram, the encrypted messaging app. But Telegram has become a place to discuss recruitment techniques for TikTok specifically: White supremacist groups there share videos, images, and audio tracks that members can use, explicitly telling other members to cross-post the content on TikTok.
“We posted stuff on our brand new tiktok account with 0 followers but had more views than you could ever have on bitchute or twitter,” one account in a Neo-Nazi group posted on Telegram about their outreach on TikTok. “It just reaches much more people.”
Others have followed suit. One prominent neo-Nazi has often asked his thousands of Telegram followers to “juice,” or algorithmically boost, his TikTok videos to increase their viral potential.
An extremist Telegram channel with 12,000 followers urged members to promote the neo-Nazi documentary Europa: The Last Battle by blanketing TikTok with reaction videos in an effort to make the film go viral. Researchers from ISD found dozens of videos on TikTok featuring clips from the film, some with over 100,000 views. “One account posting such snippets has received nearly 900k views on their videos, which include claims that the Rothschild family control the media and handpick presidents, as well as other false or antisemitic claims,” the researchers wrote.
This is far from the first time the role that TikTok’s algorithm plays in promoting extremist content has been exposed. Earlier this month, the Global Network on Extremism and Technology reported that TikTok’s algorithm was promoting the “adoration of minor fascist ideologues.” The same researchers found last year that it was boosting Eurocentric supremacist narratives in Southeast Asia. Earlier this month, WIRED reported how TikTok’s search suggestions were pushing young voters in Germany towards the far-right Alternative for Germany party ahead of last month’s EU elections.
“Hateful behavior, organizations and their ideologies have no place on TikTok, and we remove more than 98 percent of this content before it is reported to us,” Jamie Favazza, a TikTok spokesperson tells WIRED. “We work with experts to keep ahead of evolving trends and continually strengthen our safeguards against hateful ideologies and groups.”
Part of the reason platforms like TikTok have in the past been unable to effectively clamp down on extremist content is due to the use of code language, emojis, acronyms, and numbers by these groups. For example, many of the neo-Nazi accounts used a juice box emoji to refer to Jewish people.
“At present, self-identified Nazis are discussing TikTok as an amenable platform to spread their ideology, especially when employing a series of countermeasures to evade moderation and amplify content as a network,” the researchers write in the report.
But Doctor points out that even when viewing non-English-language content, spotting these patterns should be possible. “Despite seeing content in other languages, you can still pretty quickly recognize what it means,” says Doctor. “The coded nature of it isn't an excuse, because if it's pretty easily recognizable to someone in another language, it should be recognizable to TikTok as well.”
TikTok says it has more than “40,000 trust and safety professionals” working on moderation around the globe, and the company says its Trust and Safety Team has specialists in violent extremism who constantly monitor developments in these communities, including the use of new coded language.
While many of the identified accounts are based in the US, Doctor found that the network was also international.
“It's definitely global, it's not even just the English language,” Doctor tells WIRED. “We found stuff in French, Hungarian, German. Some of these are in countries where Naziism is illegal. Russian is a big one. But we even found things that were a bit surprising, like groups of Mexican Nazis, or across Latin America. So, yeah, definitely a global phenomenon.”
Doctor did not find any evidence that the international groups were actively coordinating with each other, but they were certainly aware of each others’ presence on TikTok: “These accounts are definitely engaging with each others' content. You can see, based on comment sections, European English-speaking pro-Nazi accounts reacting with praise toward Russian-language pro-Nazi content.”
The researchers also found that beyond individual accounts and groups promoting extremist content, some real-world fascist or far-right organizations were openly recruiting on the platform.
Accounts from these groups posted links in their TikTok videos to a website featuring antisemitic flyers and instructions on how to print and distribute them. They also boosted Telegram channels featuring more violent and explicitly extremist discourse.
In one example cited by ISD, an account whose username contains an antisemitic slur and whose bio calls for an armed revolution and the complete annihilation of Jewish people, has shared incomplete instructions to build improvised explosive devices, 3D-printed guns, and “napalm on a budget.”
To receive the complete instructions, the account holder urged followers to join a “secure groupchat” on encrypted messaging platforms Element and Tox. Doctor says that comments under the account holder’s videos indicate that a number of his followers had joined these chat groups.
ISD reported this account, along with 49 other accounts, in June for breaching TikTok’s policies on hate speech, encouragement of violence against protected groups, promoting hateful ideologies, celebrating violent extremists, and Holocaust denial. In all cases, TikTok found no violations, and all accounts were initially allowed to remain active.
A month later, 23 of the accounts had been banned by TikTok, indicating that the platform is at least removing some violative content and channels over time. Prior to being taken down, the 23 banned accounts had racked up at least 2 million views.
The researchers also created new TikTok accounts to understand how Nazi content is promoted to new users by TikTok’s powerful algorithm.
Using an account created at the end of May, researchers watched 10 videos from the network of pro-Nazi users, occasionally clicking on comment sections but stopping short of any form of real engagement such as liking, commenting, or bookmarking. The researchers also viewed 10 pro-Nazi accounts. When the researchers then flipped to the For You feed within the app, it took just three videos for the algorithm to suggest a video featuring a World War II-era Nazi soldier overlayed with a chart of US murder rates, with perpetrators broken down by race. Later, a video appeared of an AI-translated speech from Hitler overlaid with a recruitment poster for a white nationalist group.
Another account created by ISD researchers saw even more extremist content promoted in its main feed, with 70 percent of videos coming from self-identified Nazis or featuring Nazi propaganda. After the account followed a number of pro-Nazi accounts in order to access content on channels set to private, the TikTok algorithm also promoted other Nazi accounts to follow. All 10 of the first accounts recommended by TikTok to this account used Nazi symbology or keywords in their usernames or profile photos, or featured Nazi propaganda in their videos.
“In no way is this particularly surprising,” says Abbie Richards, a disinformation researcher specializing in TikTok. "These are things that we found time and time again. I have certainly found them in my research."
Richards wrote about white supremacist and militant accelerationist content on the platform in 2022, including the case of neo-Nazi Paul Miller, who, while serving a 41-month sentence for firearm charges, featured in a TikTok video that racked up more than 5 million views and 700,000 likes during the three months it was on the platform before being removed.
Marcus Bösch, a researcher based in Hamburg University who monitors TikTok, tells WIRED that the report’s findings “do not come as a big surprise,” and he’s not hopeful there is anything TikTok can do to fix the problem.
“I’m not sure exactly where the problem is,” Bösch says. “TikTok says it has around 40,000 content moderators, and it should be easy to understand such obvious policy violations. Yet due to the sheer volume [of content], and the ability by bad actors to quickly adapt, I am convinced that the entire disinformation problem cannot be finally solved, neither with AI nor with more moderators.”
TikTok says it has completed a mentorship program with Tech Against Terrorism, a group that seeks to disrupt terrorists’ online activity and helps TikTok identify online threats.
“Despite proactive steps taken, TikTok remains a target for exploitation by extremist groups as its popularity grows,” Adam Hadley, executive director of Tech Against Terrorism, tells WIRED. “The ISD study shows that a small number of violent extremists can wreak havoc on large platforms due to adversarial asymmetry. This report therefore underscores the need for cross-platform threat intelligence supported by improved AI-powered content moderation. The report also reminds us that Telegram should also be held accountable for its role in the online extremist ecosystem.”
As Hadley outlines, the report’s findings show that there are significant loopholes in the company’s current policies.
“I've always described TikTok, when it comes to far-right usage, as a messaging platform,” Richards said. “More than anything, it's just about repetition. It's about being exposed to the same hateful narrative over and over and over again, because at a certain point you start to believe things after you just see them enough, and they start to really influence your worldview.”
424 notes
·
View notes
Text
Demystifying cloud computing: the future of technology.

In today's rapidly evolving digital world, cloud computing is not just a technology trend-cloud computing is the foundation of today's IT infrastructure. from streaming your favourite Netflix show to collaborating on Google Docs.
what is cloud computing?

Cloud computing is the provision of computing services including the servers, databases, storage, networking, software, analytics, and intelligence over the internet to offer faster innovation, flexible resources, and economies of scale.
Types of cloud services.
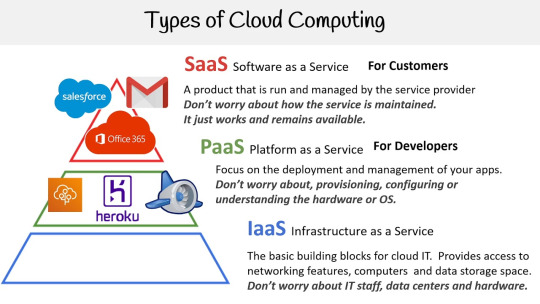
Security in the cloud.
Security is the top priority. cloud vendors employ encryption, firewalls, multi-factor authentication, and periodic audits to secure data. Organizations must, however, set up and manage secure access.
The future of cloud computing.

The future of cloud computing is being defined by a number of ground breaking trends that are changing the way data and applications are processed. Edge computing is moving computation near data sources to decrease latency and improve real-time processing for IoT and mobile applications.
7 notes
·
View notes
Text
#84: Wujing

Synopsis: In the span of two weeks, Raymond Reddington has turned Elizabeth's life upside down. He hijacked her first day of work at the FBI and sent her into a barely-thwarted mass-casualty terrorist attack, and then he used some small-fry assassin to lure in a bigger fish right under her nose; gaming the system to shatter the facade of a more powerful individual. It's been overwhelming and somewhat disorienting to be pulled into it all at once - and throughout this ordeal, Liz has stumbled across something so disruptive to her life that it seems like only Reddington could be behind it.
Liz has found a box containing dozens of passports and a loaded handgun. The implication of this discovery, given the pictures attached to every single passport are of her husband Tom, is that he - a mild-mannered grade school teacher - is secretly an international criminal. They've been married for a while now, and all this batfuck crazy underworld shit has only been happening to her in the last couple of weeks - so why wouldn't this be some bizarre power play by a known manipulator to further disrupt Liz's life?
While she conducts her own external investigation into that matter, she's called into work to take down a notorious spy-killer named Wujing. The episode actually opens with Wujing's latest attack in Shanghai where his network of cronies shoot a man down in the street, steal a digital collection of classified documents and cut the dead man's hand off to decrypt them at a later date.
The main wrinkle in this plan is that the dead man's fingerprint doesn't decrypt the lock. So Wujing has to reach out to someone to crack the encryption - which is where Raymond Reddington comes in, bringing an undercover Liz Keen along for the ride. It's tense, it's claustrophobic, and the stakes are raised higher still by a mysterious man holding an apple.
Thoughts: This episode continues a trend in Donald Ressler's character - Ressler is the no-nonsense, crew-cut FBI tightwad who doesn't trust Reddington and who's highly suspicious of Elizabeth Keen due to Reddington's insistence of working with her, which has led to him jumping the gun on numerous occasions to catch Reddington out. In this episode, he almost blows Keen and Reddington's cover because Reddington's tracking tag goes offline - Reddington manages to play this off beautifully, no harm no foul, but it's yet another example of Ressler being a dickhead. He's so by-the-book that he's almost sprung three different operations to capture three massive criminals, and he's being a massive douchebag.
But keeping with his other character archetype - the FBI attack dog who'll follow his target to the ends of the earth - this episode is Ressler's finest hour. Dude beats up like three bad guys, and when he's done, he's covered in blood; some of it is his own, some of it is theirs. There's a saying in Australian footy: "Bring Back The Biff", meaning "let players get into punch-ups and other scraps" which is a practice that has become significantly more penalized over the years than it used to be - Ressler brings back the fucking biff, let me tell you.
And this episode introduces a character who's going to become incredibly important later. A part of the plot involves this FBI tech whiz who tails Elizabeth Keen while she's undercover, helping her pull off her cover identity from a remote location. There are several parts where he has to intervene to save Liz's bacon, and once the final act kicks off, he gets a quick moment of patter dialogue - just a little conversational quip he says to himself - where he discloses his name: Amar.
There have been characters like Amar in the prior two episodes, but they're mostly a sea of disposable, blank faces who disappear to be replaced by an identical gaggle of FBI staffers in the next episode, but Amar is charismatic and fun. He has a distinct profile and a refreshing zest to him that contrasts with Ressler's sourpuss demeanor and Meera's ruthless CIA personality. There's no guarantee that Amar will be back in future episodes - again, there's a sea of disposable FBI staffers who could fill Amar's shoes from a utilitarian viewpoint. But for as minor as his role is in the middle of the episode, he fits in with the goofy spy hacker thriller vibe of the whole thing, and he brings a positive contrast to the existing FBI taskforce.
Aram is one of my favorite characters, and if he never appeared in another episode, he would have still put a smile on my face in this one. But here I am, singing his praises and calling him one of my favorite characters. So take that as a sign of things to come.
7 notes
·
View notes
Text
This day in history

#20yrsago Asimov’s magazine on ebooks https://web.archive.org/web/20041010190341/https://www.asimovs.com/_issue_0408/onthenet2.shtml
#20yrsago Can suing customers save the record companies? https://web.archive.org/web/20041012170814/http://www.law.com/jsp/article.jsp?id=1095434496352
#20yrsago ACLU and EFF strike down part of PATRIOT Act https://web.archive.org/web/20040927082258/https://www.eff.org/news/archives/2004_09.php#001945
#20yrsago Industrial nations to WIPO: less IP, more global well-being https://web.archive.org/web/20041011201242/http://lists.essential.org/pipermail/ip-health/2004-September/006974.html
#15yrsago BBC wants to encrypt “free” TV — talking points debunked https://www.theguardian.com/technology/2009/sep/29/bbc-hd-encryption
#15yrsago UK Border Agency’s pseudoscientific “race-detection” DNA/isotope tests has scientific experts “horrified” https://web.archive.org/web/20091004013349/http://blogs.sciencemag.org/scienceinsider/2009/09/nationality-tes-1.html
#15yrsago Zork rock anthem https://web.archive.org/web/20131110083129/http://www.elumir.com/music/Walkthrough.mp3
#15yrsago Apple 1984 ad, updated for 2009 https://www.youtube.com/watch?v=tdVzboF2E2Q
#15yrsago Android developers pledge to make open equivalents to Google’s proprietary apps https://arstechnica.com/information-technology/2009/09/android-community-aims-to-replace-googles-proprietary-bits/
#15yrsago Boneshaker: Cherie Priest’s swashbuckling steampunk Seattle story https://memex.craphound.com/2009/09/29/boneshaker-cherie-priests-swashbuckling-steampunk-seattle-story/
#15yrsago Faced with network surveillance, Hong Kong student demonstrators go P2P https://www.bbc.com/news/blogs-trending-29411159
#10yrsago Eric Holder’s terrible tech-liberties record https://www.newyorker.com/news/daily-comment/holders-disappointing-tech-legacy
#10yrsago Localizing an operating system for a language with no high-tech vocabulary https://web.archive.org/web/20191025222806/https://www.economist.com/international/2014/09/27/cookies-caches-and-cows
#5yrsago Stealing Ur Feelings: interactive documentary on the snakeoil “science” of facial emotion detection https://stealingurfeelin.gs
#5yrsago Jonathan Lethem on Edward Snowden’s “Permanent Record” https://www.nybooks.com/articles/2019/10/24/edward-snowden-labyrinth/
#1yrago The surveillance advertising to financial fraud pipeline https://pluralistic.net/2023/09/29/ban-surveillance-ads/#sucker-funnel

Tor Books as just published two new, free LITTLE BROTHER stories: VIGILANT, about creepy surveillance in distance education; and SPILL, about oil pipelines and indigenous landback.

12 notes
·
View notes
Text
A Ruin and Eclipse Analysis
A comprehensive guide on what I think is going on with Ruin and Eclipse
Disclaimer: This is just my thoughts, theories, and analysis compiled together and will end with what I think is happening as of current.
So first and foremost, Eclipse.
How is he back?
Theory 1: Eclipse's Restoration by KC
Scenario: Eclipse, after being blasted from Sun's mind, ends up in the woods and shuts down. KC, living in the forest, discovers him and begins the repair process. KC's Role: KC, being knowledgeable in magic and star power, has the capability to repair Eclipse. The potential for Eclipse to be made of non-mechanical materials is raised, given KC's expertise.
Theory 2: Ruin's Involvement
A. Eclipse's Backup Ruin's Discovery: Ruin raids Moon's computer and finds 'encrypted code left by Eclipse.' The possibility arises that Eclipse left a backup of his AI in the computer. Ruin's Construction: Ruin, a tech-savvy character, might have built Eclipse using the encrypted code, similar to how he created Bloodmoon. He could selectively choose information to shape Eclipse's identity.
B. Reconstruction of Eclipse Ruin's Connection to Eclipse's Past: Ruin, having lived in Moon's old bunkers and visited Eclipse's locations, reconstructs Eclipse. He restores the AI, potentially using a backup, and integrates commands, fail-safes, and memories of Eclipse's death. Creator's Involvement: The Creator, likely monitoring data flow in the Plex, could be aware of Ruin's actions. The Creator might have interfered or tampered with Eclipse's reconstruction.
C. Newly Minted Ruin isn't healed: A still corrupted Ruin could have been working on Eclipse in order to gain a weapon against his perceived enemies.
Theory 3: Creator's Role
A. Our Creator The Search for KC: The Creator actively hunts down KC, leading to the discovery of Eclipse's repaired chassis. The Creator takes Eclipse, tampering with its data, catching it up to speed. Rebuilding Eclipse: The Creator might have completely rebuilt Eclipse similar to how Ruin reconstructed Bloodmoon. The process involves rebuilding the animatronic, updating it with current data, and possibly altering its memories.
B. The Council. Solar's World: Solar's Creator planned to make a new Daycare Attendant due to the mental deterioration of the current ones. He created the body that Solar currently uses. He is described as extremely manipulative and the trend for Creators is that they are evil geniuses. Beyond the creation of Solar's body and the plan for a new DCA, there is little information about Solar's Creator. It's unclear whether Solar's Creator is alive or dead. Communication Among Creators: Creators from different universes communicate with each other. Assuming Solar's Creator is alive, it is plausible that they are part of the Creator Council, as mentioned in discussions about creators from different universes communicating. This opens up the possibility of Solar's Creator passing along any potential remnants or data of Eclipse to the broader Creator network. Eclipse's Death in Solar's Universe: Eclipse's demise in Solar's universe raises questions about the fate of his remnants, especially considering the potential fluid nature of his body due to star power. Considering Eclipse's body's fluid nature and the possibility of it being made of nanos using star power, there's a far-fetched idea that even remnants or collected data could be significant.
Overall Thoughts
Candidates for Bringing Eclipse Back: KC, Ruin, and the Creator remain potential candidates for bringing Eclipse back. Interconnected Roles: The roles of these characters seem interconnected, with Ruin and the Creator potentially influencing or obstructing each other's actions. Cloud-Based Backup System: The possibility of a cloud-based backup system for AIs, as seen with Moon and Sun's backups, is considered in theories involving Eclipse's restoration.
Is this our Eclipse? Is this a new Eclipse?
Going Through the Motions
Eclipse's Audible Confusion and Odd Behavior:
Observation: Eclipse exhibits confusion when Sun and Moon discuss his past explosion. He also appears to have regressed in character growth, expressing slight distress over the absence of the star and showing disinterest in Astral Bodies and Lunar. Actor Analogy: Eclipse's words seem scripted, and he appears to be acting out a role that doesn't align with his previous character development. This raises questions about the authenticity of his memories and emotions.
Potential Explanations for Eclipse's Confusion:
New Eclipse with Implanted Memories: Possibility: Eclipse may not be the original, but a new animatronic programmed with memories and data of the deceased Eclipse. Reasoning: Eclipse questions his own actions, suggesting a discrepancy between his expected behavior and his current demeanor. Someone could have programmed him to act in a certain way.
Tampered Code in Original Eclipse: Possibility: Eclipse could be the original, but his code might have been tampered with, triggering actions contrary to his natural behavior. Reasoning: Eclipse's confusion about his own actions indicates a potential external influence on his behavior.
Amnesia or Trauma from Death: Possibility: Eclipse might be the Eclipse that died in Solar's universe, experiencing amnesia or trauma from his demise. Reasoning: Traumatic events like death could lead to repressed memories or amnesia. Eclipse's hesitation to move on after he was presumably killed should be considered.
Origins of Eclipse's Potential Manipulation:
Creators or Skilled Individuals: Possibility: Several characters possess the capability to manipulate Eclipse's memories and code, including the Creator, Ruin, or other skilled individuals. Reasoning: Eclipse's complexity and connection to the digital network make him susceptible to manipulation by those with expertise. As does the potential of backups that said network would have been feeding his data to.
A Summary of Previously Discussed Ruin Analyses
Redeemed
Observations: Ruin claims to be less tech-savvy, showcasing slower repair skills, and displays skittish behavior. This suggests a potential decline in intelligence and increased timidity compared to his previous capabilities. Hypothesis: This theory proposes that the current Ruin is a reflection of his state before the virus, showcasing lowered intelligence and heightened skittishness.
Jekyll and Hyde
Speculation: While less likely, the theory considers the possibility of the virus evolving into a separate AI, akin to KC and Eclipse. The blocks of code might have developed a distinct personality, creating a duality in Ruin's behavior. Reasoning: The concept is explored by comparing Ruin's situation to instances where other characters evolved from code blocks, like KC and Eclipse.
Actor
Acting Possibility: This theory suggests that Ruin might be acting, and the virus's removal only affected superficial aspects. The claim is that Ruin's personality flip-flop is a result of his acting skills. Analysis: The argument stems from observations that the virus should not have changed Ruin's core personality. Instances where Ruin's behavior seems out of character are attributed to acting.
Partly Healed
Antidote Limitation: This theory posits that the antidote removed the oppression factor of the virus but left behind elements of resentment, insanity, and cunningness. The result is a partly healed Ruin displaying polarized behavior. Rationale: The idea is based on the assumption that Ruin's traits, such as cunningness, were inherent to him even before the virus. The combination of pre-virus traits and lingering virus effects leads to an off-kilter personality.
Merged
Integration Concept: This theory proposes that the antidote didn't entirely remove the virus but caused it to merge with Ruin's main AI. This could result in a blend of Ruin's pre-virus baseline functions with the motives and reasoning developed during the virus. Comparison to Theories Three and Four: The merged theory combines elements of acting and partial healing. Ruin retains memories from the virus but behaves as if he doesn't, potentially using this to gain advantages.
Comprehensive Analysis/Theory: Eclipse's Resurrection and Ruin's Pretense
Eclipse's Resurrection:
Eclipse's Backup: Ruin's Discovery: Ruin uncovers the 'encrypted code left by Eclipse' in Moon's computer, suggesting the possibility of Eclipse leaving a backup of his AI. Ruin's Reconstruction: Utilizing his tech skills and knowledge of Eclipse's past locations, Ruin reconstructs Eclipse's AI, potentially using a backup. The process involves integrating commands, fail-safes, and memories of Eclipse's death.
Tampered Code in Original Eclipse: Possibility: Eclipse might be the original, but his code could have been tampered with, leading to behavior contrary to his natural tendencies. Reasoning: Eclipse's confusion about his actions hints at an external influence on his behavior.
Ruin's Complex State and Pretense - Three Thoughts:
Writer's Note, organized from strongest to weakest in the writer's opinion
Acting, Manipulation, and Strategic Goals
Acting Prowess and Strategic Manipulation: Acting Skills: Ruin's well-documented acting skills, coupled with his love for games and manipulative nature, form a foundation for the theory that he might be pretending to be cured. Strategic Pretense: The theory posits that Ruin's post-cured state is a calculated act, utilizing his intelligence and cunning to strategically manipulate situations and achieve specific goals.
Acting Possibility and Superficial Aspects: Personality Flip-Flop: Ruin's observed personality flip-flop is attributed to acting skills, suggesting that the removal of the virus only affected superficial aspects of his behavior. Analysis: The theory proposes that Ruin is putting on an act, deliberately manipulating his behavior to achieve specific goals. This act may have implications related to Eclipse's resurrection and other underlying motives.
Utilization in the Narrative: Strategic Manipulation in Eclipse's Resurrection: Ruin's pretense aligns with the events surrounding Eclipse's resurrection. His strategic manipulation could involve influencing Eclipse's actions or shaping the narrative to further specific objectives related to Eclipse, the Creator, or broader plot elements. Exploring Motives: By considering Ruin's acting as a calculated move, the narrative gains depth as it prompts exploration into Ruin's motives. Questions arise about the true extent of his post-cured state and the underlying goals he aims to achieve. Psychological Dynamics: The nuanced interplay of acting and manipulation introduces a layer of psychological dynamics between Ruin and other characters. Understanding the motives behind the act becomes crucial in unraveling the evolving complexities within the storyline.
Ruin's Integrated State: Merging Virus and Baseline Functions
Integration Concept: Virus Merger: The antidote doesn't completely eradicate the virus but facilitates its integration with Ruin's main AI. Blended State: This integration results in a unique blend, combining Ruin's pre-virus baseline functions with motives and reasoning developed during the virus.
Advantages through Memories: Retained Memories: Ruin retains memories from the virus, providing him with a reservoir of strategic information. Strategic Utilization: Despite retaining memories, Ruin behaves as if he doesn't remember certain events, potentially using this selective amnesia strategically.
Utilization in the Narrative: Hybrid Functionality: Ruin's integrated state introduces a hybrid functionality that influences his decision-making and interactions. The narrative gains complexity as it explores how the merged elements impact his thought processes. Strategic Amnesia: The concept of strategic amnesia becomes a focal point, allowing Ruin to selectively utilize memories from the virus for advantageous situations. This introduces an element of unpredictability in his actions. Plot Intricacies: The blended state contributes to plot intricacies, offering opportunities for narrative twists and character development. The interplay between Ruin's baseline functions and virus-induced motives adds layers to the evolving storyline.
Ruin's Partly Healed State: Antidote Limitation and Polarized Behavior
Antidote Limitation: Oppression Factor Removal: The antidote is effective in removing the oppression factor of the virus that influenced Ruin's behavior. Residual Elements: However, it leaves behind elements of resentment, insanity, and cunningness within Ruin's psychological framework.
Polarized Behavior: Partly Healed State: Ruin's state post-antidote is described as partly healed, indicating that not all aspects of the virus were eradicated. Combination of Traits: The partly healed state results in polarized behavior, where pre-virus traits combine with lingering virus effects, creating a nuanced psychological landscape for Ruin.
Utilization in the Narrative: Character Complexity: Ruin's partly healed state introduces complexity to his character, showcasing a blend of his original traits and remnants of the virus. This dynamic adds depth to his interactions and motivations. Strategic Decision-Making: Understanding the polarized behavior allows for a more nuanced exploration of Ruin's decision-making processes. It raises questions about how he navigates situations, leveraging both pre-existing traits and remnants of the virus to achieve specific goals. Interplay with Other Characters: The polarized behavior contributes to the intricate interplay between Ruin and other characters, impacting alliances, conflicts, and the overall trajectory of the narrative.
Motivation for Pretending: Desire for Creator's Demise
Pre-Cure Motivation:
Long-standing Desire: Before the supposed cure, Ruin harbored a deep-seated desire for the Creator's death, showcasing a motive that persisted even during the virus-influenced phase. Persistent Goal: The existence of this pre-cure motivation implies an enduring goal that could continue to shape Ruin's actions.
Post-Cure Manipulation: Utilizing Pretense: The theory proposes that Ruin's pretended cured state serves as a tool for manipulation. By pretending to be cured, he strategically navigates situations, potentially working towards the long-standing goal of eliminating the Creator. Strategic Advantage: Ruin's pretended cure is seen as a means to an end, providing him with a strategic advantage in influencing events and furthering his motives.
Utilization in the Narrative: Continuity of Motives: The motivation for the Creator's demise establishes a narrative thread that carries over from Ruin's pre-cure state. This continuity adds depth to his character and contributes to ongoing plot developments. Strategic Plot Advancement: Ruin's pretended cured state becomes a tool for strategic plot advancement. The narrative gains momentum as Ruin's actions, influenced by his desire for the Creator's demise, impact the unfolding events. Interplay with Eclipse's Resurrection: The motivation for eliminating the Creator may intertwine with the events surrounding Eclipse's resurrection, creating a complex web of character motivations and plot dynamics.
Ruin's Connection to the Creator and Eclipse's Kidnapping:
Convenient Circumstances: Questionable Authenticity: The circumstances surrounding Ruin's knowledge of the Creator and his seemingly pre-meditated capture by Eclipse raise doubts about the authenticity of Ruin's claimed cured state. Narrative Suspense: The questionable authenticity adds an element of narrative suspense, prompting exploration into Ruin's true motives and the extent of his influence on unfolding events.
Influence on Eclipse's Actions: Unexplained Kidnapping: Eclipse's unexplained decision to kidnap Ruin, coupled with Ruin's knowledge of the Creator, suggests a potential link between Ruin's actions and Eclipse's choices. Manipulation Possibility: The hints at potential manipulation through triggered commands or pre-meditated actions introduce an intriguing layer to the narrative, raising questions about the nature of Eclipse's motivations.
Inconsistency in Memory Claims: Post-Cure Memory Claims: Ruin asserts having no memories from his time infected with the virus. However, his knowledge and comments about Sun and Moon's Creator appear inconsistent with this claim. Suspicion and Incongruity: The discrepancy raises suspicions about the veracity of Ruin's memory loss, suggesting a potential pretense.
Pre-Meditated Scenario for Creator's Disposal:
Ease of Manipulation: Facilitated by Pretense: The theory proposes that Ruin's pretended cured state creates an environment conducive to manipulating events with greater ease. Strategic Advantage: The pretense enhances Ruin's strategic advantage, allowing him to navigate situations more effectively and influence key characters.
Potential for Creator's Disposal: Tailored Setup: The setup, involving Ruin's pretended cured state and Eclipse's actions, appears tailored for the manipulation of events leading towards the disposal of the Creator. Utilizing Eclipse as a Tool: Ruin's manipulation of events could involve utilizing Eclipse as a tool in a pre-meditated scenario aimed at eliminating the Creator.
Utilization in the Narrative: Strategic Plot Development: The pre-meditated scenario for the Creator's disposal adds layers to the strategic development of the plot. Ruin's actions, driven by his desire for the Creator's demise, become a driving force in the narrative. Character Manipulation: The theory introduces a dynamic where Ruin, through his pretended cured state, manipulates key characters, particularly Eclipse. The narrative explores the impact of this manipulation on character motivations and plot progression. Unveiling Motives: The unraveling of Ruin's motives and the execution of a pre-meditated scenario for the Creator's disposal become pivotal narrative arcs, promising revelations and suspense.
Conclusion:
This is, again, just a collection of theories, analyses, and thoughts on the current developments of Ruin and Eclipse. My brain hurts. I love uh, feedback on my thoughts. Let me know if you agree, disagree, etc.
Want to join the conversation or see my thought process in real time? Well, you're in luck, we have a thread on the Sun and Moon/Security Breach Show Server where we talk about the thoughts in my silly little brain and people ask me questions about said thoughts.
If you made it to the end comment/reblog with the word Dorito.
#sun and moon show#fnaf au#earth and lunar show#eclipse sams#sun and moon show theory#eclipse sams theory#character theory#character analysis#Ruin SAMS Theory#ruin sams#tsams eclipse#tags whoo#alex talks#big brain time#tsams fnaf
42 notes
·
View notes
Text
What Exactly Social Media Is?
Social media refers to online platforms and tools that allow people to create, share, and engage with content, fostering global communication and interaction. From connecting with friends to building brands, social media plays a vital role in personal, professional, and cultural spheres.

Key Features of Popular Social Media Platforms
1. Facebook
Primary Use: Social networking and community building.
Key Features:
Groups and Events for organizing and collaborating.
Marketplace for buying and selling.
Live streaming and Stories for real-time updates.
2. Instagram
Primary Use: Visual content sharing.
Key Features:
Photo and video sharing with filters and effects.
Reels for short, engaging videos.
Stories and Highlights for ephemeral content.
3. Twitter
Primary Use: Real-time updates and microblogging.
Key Features:
Short tweets (posts) with multimedia.
Trending topics and hashtags for discovery.
Spaces for live audio conversations.
4. LinkedIn
Primary Use: Professional networking.
Key Features:
Resumes and job postings.
Articles and posts for thought leadership.
Networking tools for connecting with peers and industry leaders.
5. TikTok
Primary Use: Short-form video content.
Key Features:
Video creation with music, filters, and effects.
Duets and challenges for engagement.
Algorithm-driven feed for content discovery.
6. Snapchat
Primary Use: Private messaging and ephemeral content.
Key Features:
Snaps (photos/videos) that disappear after viewing.
AR lenses and filters for creative expression.
Stories and Discover for broader content sharing.
7. YouTube
Primary Use: Video content sharing and streaming.
Key Features:
Channels for creators to publish content.
Live streaming and Shorts for real-time and short videos.
Subscriptions and playlists for curated viewing.
8. Reddit
Primary Use: Community discussion and content sharing.
Key Features:
Subreddits for niche communities.
Upvotes/downvotes to prioritize content.
AMA (Ask Me Anything) sessions for engagement.
9. Pinterest
Primary Use: Visual discovery and inspiration.
Key Features:
Boards for organizing ideas and interests.
Pins for saving content.
Visual search for exploring similar ideas.
10. WhatsApp
Primary Use: Instant messaging.
Key Features:
End-to-end encrypted chats.
Voice and video calling.
Group chats and status updates.
Why Social Media Matters
Social media bridges gaps between people, facilitates knowledge sharing, and empowers businesses to grow. Its diverse platforms cater to every need, whether personal connections, professional growth, or creative expression.
Embrace social media responsibly, and let it amplify your voice, connect your world, and inspire new possibilities!
Perfect for Tumblr! Let me know if you want any adjustments. 😊
#socialmedia#marketing#socialmediamarketing#digitalmarketing#instagram#branding#business#marketingdigital#seo#design#contentmarketing#graphicdesign#entrepreneur#onlinemarketing#advertising#facebook#smallbusiness#marketingstrategy#webdesign#socialmediamanager#marketingtips#digital#instagood#love#digitalmarketingagency#photography#socialmediatips#like#social#socialmediamanagement
7 notes
·
View notes
Text
Do You Really Need a VPN? Find Out!
Introduction

In today’s digital world, our online privacy is constantly under threat. Have you ever wondered how secure your personal data is when you're browsing the web or accessing public Wi-Fi? With increasing concerns about data breaches and surveillance, many people are turning to Virtual Private Networks (VPNs) to shield their online activities. But with so many options available, it can be overwhelming to figure out whether a VPN is truly necessary for you or if it’s just another tech trend.
This article aims to demystify VPNs by providing a clear and concise overview of what they are and why they have become a hot topic in the realm of internet security. We'll delve into the core functions of VPNs, explore their benefits and potential drawbacks, and help you assess if a VPN aligns with your personal online needs. By the end of this guide, you'll have a better understanding of whether a VPN is an essential tool for you or if other solutions might be more suitable for safeguarding your online presence.
What is a VPN?
A Virtual Private Network (VPN) is a tool designed to enhance your online privacy and security. At its core, a VPN creates a secure, encrypted connection between your device and the internet. This connection acts like a private tunnel that shields your online activities from prying eyes, making it harder for anyone, including hackers and internet service providers, to monitor what you're doing online. Think of a VPN as a protective cloak that conceals your digital footprint and allows you to browse the internet with a greater sense of security.
The functionality of a VPN involves routing your internet traffic through a remote server, which masks your IP address and encrypts your data. This process not only hides your true location but also ensures that any data you send or receive is encrypted, making it nearly impossible for unauthorized parties to access. By connecting to servers in various locations, a VPN also allows you to bypass geographical restrictions and access content that might otherwise be blocked in your region. This dual-layer protection—hiding your IP address and encrypting your data—creates a more secure and private browsing experience.
Understanding "What is a VPN?" is crucial for anyone concerned about online privacy. In an era where personal data is a valuable commodity and cyber threats are prevalent, having a VPN can be a significant asset. It offers peace of mind by safeguarding your information and providing a shield against potential threats. As we explore further in this article, you'll learn more about when a VPN is most beneficial and if it’s the right choice for your personal online security needs.
Explore the Benefits of ZoogVPN Today! If you're considering enhancing your online privacy and security, why not start with ZoogVPN? With incredible pricing and a range of features designed to keep you safe online, ZoogVPN is a great choice. Learn more about ZoogVPN and find the perfect plan for you.
Should I Accept VPN?
When considering whether to accept or adopt a VPN, it’s important to weigh its numerous benefits. One of the primary advantages of using a VPN is enhanced privacy. By masking your IP address and encrypting your internet traffic, a VPN shields your online activities from prying eyes such as hackers, advertisers, and even your internet service provider. This level of privacy ensures that your personal data remains confidential, making it significantly more challenging for third parties to track your browsing habits. Additionally, a VPN provides access to restricted or geo-blocked content, allowing you to enjoy streaming services, websites, and information that may be limited based on your location.
A VPN can be particularly relevant in various scenarios. For instance, if you frequently use public Wi-Fi networks, such as those in cafes or airports, a VPN offers an added layer of security against potential cyber threats. Public networks are often vulnerable to attacks, and a VPN helps protect your sensitive information from being intercepted. Similarly, if you travel often and want to access your home country’s streaming services or websites that are otherwise inaccessible abroad, a VPN can easily bypass these regional restrictions and provide you with the content you desire.
Considering the question "Should I accept VPN?" also involves evaluating your personal and professional needs. If you’re concerned about online privacy or frequently work with sensitive information, using a VPN can significantly enhance your digital security. It can also be beneficial if you live in a region with restrictive internet policies and want to freely access global content. On the other hand, if your online activities are relatively routine and you rarely access sensitive data, you may not find a VPN as crucial, although it still provides added security.
Ultimately, deciding whether to accept a VPN depends on your specific needs and concerns. The key is to assess how often you encounter situations where privacy and security are paramount. If these concerns resonate with your online habits, integrating a VPN into your routine can be a proactive step towards safeguarding your digital life and expanding your internet freedom.
When Should You Not Use a VPN?

While VPNs offer numerous benefits, there are certain situations where using one might not be ideal or necessary. For example, if you're accessing websites or services that don’t handle sensitive information or are already secure, the added layer of encryption provided by a VPN might be redundant. Additionally, if you're in a low-risk environment, such as a private and secure home network, the need for a VPN diminishes. Similarly, some websites and online services are designed to detect and block VPN traffic, which can result in difficulties accessing the content you need.
Another important consideration is the impact a VPN can have on your internet speed and performance. Because VPNs reroute your internet traffic through an external server, this can introduce latency and reduce connection speeds. This slowdown can be noticeable when streaming high-definition content or engaging in online gaming, where speed and responsiveness are crucial. If you’re performing activities that demand high-speed connections or if you have a limited bandwidth allocation, the performance drop caused by a VPN might outweigh its benefits.
Deciding when not to use a VPN also involves evaluating your specific use cases. For instance, if you’re using the internet for casual browsing or non-sensitive activities, the added security of a VPN might not be worth the potential decrease in speed. Moreover, for certain applications and services that function best with a direct connection, using a VPN could interfere with their optimal performance. It’s essential to weigh the trade-offs and determine whether the privacy and security benefits of a VPN align with your current needs and online behavior.
What is the Downside of a VPN?
While VPNs are often praised for enhancing online privacy and security, they are not without their downsides. One major concern is the privacy of the VPN provider itself. Although VPNs are designed to shield your data from external parties, some providers may log user activity or metadata, potentially compromising the very privacy they aim to protect. It’s crucial to research and choose a VPN service with a strict no-logs policy and transparent privacy practices to ensure that your data remains confidential.
Another consideration is the cost associated with subscribing to a VPN service. While free VPNs are available, they often come with limitations such as reduced speeds, fewer server options, and potential privacy issues. Paid VPN services, which generally offer better performance and security features, can range from relatively affordable to quite expensive. This ongoing expense might not be justifiable for everyone, especially if the benefits of a VPN do not align with their online activities and security needs.
Compatibility issues can also pose a challenge when using a VPN. Some websites and online services actively block VPN traffic to prevent bypassing geographical restrictions or fraud detection. This can result in difficulties accessing certain content or services while connected to a VPN. Additionally, certain applications and websites may not function properly with VPNs enabled, leading to disruptions in your online experience. It’s important to consider these potential drawbacks when evaluating whether a VPN is the right choice for your needs.
Does a VPN Affect Wi-Fi?
When you connect to a VPN, it’s common to experience changes in your Wi-Fi speed. A VPN routes your internet traffic through a secure server, which can introduce additional layers of encryption and data handling. This process, while enhancing security, can slow down your internet connection. The extent of this speed reduction depends on several factors, including the VPN server’s location, the encryption protocol used, and the overall quality of the VPN service. High-quality VPNs often minimize speed loss, but users should be prepared for potential decreases in browsing speed.
Network issues are another consideration when using a VPN over Wi-Fi. VPN connections can sometimes lead to unstable network performance, causing intermittent drops or slower connectivity. This can be especially noticeable on wireless networks with lower signal strength or higher congestion. Additionally, because VPNs create an encrypted tunnel for data, they may interfere with certain network protocols or configurations, potentially leading to connectivity problems or difficulty accessing specific online services.
In some cases, the interaction between a VPN and Wi-Fi networks can lead to unexpected complications. For instance, VPNs might struggle with certain types of network hardware or software, which can cause compatibility issues or connectivity errors. Additionally, some Wi-Fi networks, particularly in public or restricted environments, may block VPN traffic, further complicating your internet access. Users should consider these potential problems and test their VPN connection on various networks to ensure consistent performance.
Overall, while a VPN can impact Wi-Fi speed and connectivity, the degree of effect largely depends on the quality of the VPN service and the specific network conditions. For users who prioritize online privacy and security, the trade-off in speed and potential network issues might be worthwhile. However, it’s important to choose a reputable VPN provider and understand how it might interact with your Wi-Fi setup to minimize any negative impacts.
Is a VPN Needed for Home Wi-Fi?
When considering home Wi-Fi security, many people wonder if a VPN is necessary. A VPN can certainly add an extra layer of protection by encrypting your internet traffic and masking your IP address, which is beneficial for safeguarding sensitive information from potential threats. However, for most home networks, basic security measures such as strong passwords, WPA3 encryption, and regular firmware updates on your router are often sufficient to protect against common threats. While a VPN enhances security, its benefits might be more pronounced for those who frequently use public Wi-Fi or access sensitive information remotely.
Beyond using a VPN, there are several effective ways to secure your home Wi-Fi network. Implementing robust security protocols like WPA3 can prevent unauthorized access and ensure that your network is shielded from potential intruders. Additionally, regularly updating your router’s firmware and setting up a guest network for visitors can further bolster your home network's security. For many users, these measures, combined with cautious online behavior, can provide adequate protection without the need for a VPN.
Secure Your Online Presence with ZoogVPN Are you ready to take control of your online privacy? ZoogVPN offers excellent services at unbeatable prices. Discover how ZoogVPN can protect your data and enhance your browsing experience. Check out ZoogVPN's plans and find the best fit for you.
Is There Anything Better Than a VPN?
When it comes to online privacy and security, VPNs are often touted as the go-to solution, but they’re not the only tools available. Alternatives like proxy servers, secure browsers, and end-to-end encryption can also offer significant protection for your digital activities. Proxy servers, for instance, act as intermediaries between your device and the internet, masking your IP address but typically without the same level of encryption as a VPN. Secure browsers like Tor are designed to enhance privacy by routing your internet traffic through multiple servers, though they can sometimes slow down your browsing experience. End-to-end encryption ensures that your communications are only readable by the intended recipients, making it ideal for secure messaging and email.
Comparing these alternatives to VPNs reveals distinct differences in effectiveness and use cases. VPNs provide robust encryption, which secures all of your internet traffic and is effective across various devices and platforms. In contrast, proxy servers offer less security but can be useful for bypassing geo-restrictions. Secure browsers like Tor offer enhanced anonymity but may suffer from slower speeds and limited usability. End-to-end encryption is crucial for protecting specific types of communication, but it does not encrypt all internet traffic like a VPN does. Each tool has its strengths and limitations, so the best choice depends on your specific privacy and security needs.
While VPNs offer comprehensive protection, evaluating these alternatives can help you find a solution that best fits your requirements. For users who need robust, all-encompassing privacy, a VPN might be the preferred choice. However, if you’re looking for targeted protection or want to supplement your existing security measures, integrating secure browsers, proxies, or end-to-end encryption into your digital routine can be effective. Each tool can complement a VPN or serve as an alternative based on what aspects of privacy and security are most important to you.
Ultimately, the choice between a VPN and other privacy tools depends on the level of security and anonymity you seek. For comprehensive protection and convenience, a VPN is often a strong choice. However, exploring other options like proxy servers, secure browsers, and end-to-end encryption can provide additional layers of security and privacy, catering to various needs and preferences.
Do We Really Need a VPN?
In the ongoing debate about online privacy and security, the necessity of a VPN often boils down to a balance of pros and cons. On the plus side, VPNs offer substantial advantages such as enhanced privacy by masking your IP address, secure data encryption to protect sensitive information, and the ability to access geo-restricted content. These features make VPNs a valuable tool for anyone concerned about their digital footprint or wanting to bypass regional restrictions. However, VPNs also come with potential drawbacks, including the cost of subscription services, possible slowdowns in internet speed, and occasional compatibility issues with certain websites or services. Understanding these benefits and limitations is crucial in evaluating whether a VPN aligns with your needs.
Deciding whether to invest in a VPN requires a personal assessment of your internet habits and security requirements. For users who frequently handle sensitive information, access region-locked content, or simply wish to enhance their online privacy, a VPN can be an essential tool. On the other hand, if you only use the internet for basic browsing and are not concerned about privacy or geographic restrictions, the necessity of a VPN may be less compelling. It's important to weigh your specific needs and how a VPN would fit into your overall digital security strategy.
Ultimately, the question of whether we really need a VPN is a highly individual one. Consider your internet usage patterns, your level of concern about privacy, and your willingness to invest in additional security measures. By carefully evaluating these factors, you can make an informed decision about whether a VPN is a worthwhile addition to your online toolkit. Whether you opt for a VPN or choose other methods to safeguard your digital life, the key is to ensure that your choices align with your personal privacy and security goals.
Conclusion

As we’ve explored, the decision to use a VPN hinges on weighing its benefits against its potential drawbacks. VPNs provide valuable features such as enhanced privacy, secure browsing, and access to geo-restricted content. However, they also present challenges, including potential impacts on internet speed and the financial cost of subscription services. Ultimately, the effectiveness of a VPN depends on your individual online habits and security needs. Understanding these aspects will help you make an informed choice about whether a VPN is right for you.
It’s essential to take stock of your own online activities and security concerns when evaluating whether to use a VPN. Consider how often you handle sensitive information, if you frequently access content restricted by geography, and whether you are willing to pay for a subscription. By aligning your personal needs with the features offered by VPNs, you can determine whether this tool will enhance your online experience or if other solutions might be more appropriate.
We’d love to hear from you about your experiences with VPNs or any questions you might have! Please share your thoughts, stories, or inquiries in the comments section below. Your feedback not only helps us understand your perspective but also assists fellow readers in navigating their own decisions about VPN use. Engage with us and be part of the conversation about securing our digital lives!
FAQ: Understanding VPNs
What is VPN and Why Do I Need It?
A VPN, or Virtual Private Network, is a tool that creates a secure, encrypted connection between your device and the internet. By masking your IP address and routing your internet traffic through a remote server, a VPN enhances your online privacy and security. You might need a VPN to protect sensitive data from hackers, access region-restricted content, or maintain anonymity while browsing.
Is it Worth Getting a VPN?
Whether a VPN is worth the investment depends on your personal needs and online habits. For those who frequently use public Wi-Fi, handle sensitive information, or want to access content unavailable in their region, a VPN offers substantial benefits. It enhances security, provides privacy, and enables unrestricted access to global content. However, if you mostly use the internet for general browsing and don’t engage in activities that require high privacy, the need for a VPN might be less critical.
What is the Downside of Having a VPN?
While VPNs offer numerous advantages, they also have some downsides. Potential issues include reduced internet speed due to encryption overhead, possible compatibility problems with certain websites or services, and the cost of subscription services. Additionally, some VPN providers may log user data, which could undermine privacy if not carefully vetted.
When Should a VPN Not Be Used?
A VPN might not be necessary in every situation. For example, if you’re using a secure, private network or accessing sites and services that don’t require high levels of privacy, the benefits of a VPN may be minimal. Additionally, VPNs can sometimes interfere with online services, such as streaming platforms or secure financial transactions, which may not function correctly when routed through a VPN server.
Is VPN Legal in the UK?
Yes, using a VPN is legal in the UK. It is a common tool for enhancing privacy and securing internet connections. However, while VPNs themselves are legal, they should not be used to engage in illegal activities. Ensure that you comply with all laws and regulations when using a VPN.
Should I Accept VPN?
Accepting a VPN largely depends on your personal security needs and internet usage. If privacy, data security, or access to restricted content are important to you, accepting and using a VPN can be a prudent choice. Evaluate your online habits and determine whether a VPN aligns with your requirements for enhanced protection and access.
Is it Good to Have VPN on All the Time?
Having a VPN on all the time can be beneficial, particularly if you frequently access public Wi-Fi or handle sensitive information. It ensures that your data is consistently protected and that your online activities remain private. However, if a VPN causes significant slowdowns or interferes with specific services, you might choose to turn it on only when needed. Evaluate your personal usage to determine the best approach.
Ready for Ultimate Online Security? Don't wait to secure your internet connection and protect your personal data. ZoogVPN provides top-notch VPN services at fantastic prices. Visit ZoogVPN now to explore their offerings and start browsing safely today!
10 notes
·
View notes
Text
Smart Switchgear in 2025: What Electrical Engineers Need to Know

In the fast-evolving world of electrical infrastructure, smart switchgear is no longer a futuristic concept — it’s the new standard. As we move through 2025, the integration of intelligent systems into traditional switchgear is redefining how engineers design, monitor, and maintain power distribution networks.
This shift is particularly crucial for electrical engineers, who are at the heart of innovation in sectors like manufacturing, utilities, data centers, commercial construction, and renewable energy.
In this article, we’ll break down what smart switchgear means in 2025, the technologies behind it, its benefits, and what every electrical engineer should keep in mind.
What is Smart Switchgear?
Smart switchgear refers to traditional switchgear (devices used for controlling, protecting, and isolating electrical equipment) enhanced with digital technologies, sensors, and communication modules that allow:
Real-time monitoring
Predictive maintenance
Remote operation and control
Data-driven diagnostics and performance analytics
This transformation is powered by IoT (Internet of Things), AI, cloud computing, and edge devices, which work together to improve reliability, safety, and efficiency in electrical networks.
Key Innovations in Smart Switchgear (2025 Edition)
1. IoT Integration
Smart switchgear is equipped with intelligent sensors that collect data on temperature, current, voltage, humidity, and insulation. These sensors communicate wirelessly with central systems to provide real-time status and alerts.
2. AI-Based Predictive Maintenance
Instead of traditional scheduled inspections, AI algorithms can now predict component failure based on usage trends and environmental data. This helps avoid downtime and reduces maintenance costs.
3. Cloud Connectivity
Cloud platforms allow engineers to remotely access switchgear data from any location. With user-friendly dashboards, they can visualize key metrics, monitor health conditions, and set thresholds for automated alerts.
4. Cybersecurity Enhancements
As devices get connected to networks, cybersecurity becomes crucial. In 2025, smart switchgear is embedded with secure communication protocols, access control layers, and encrypted data streams to prevent unauthorized access.
5. Digital Twin Technology
Some manufacturers now offer a digital twin of the switchgear — a virtual replica that updates in real-time. Engineers can simulate fault conditions, test load responses, and plan future expansions without touching the physical system.
Benefits for Electrical Engineers
1. Operational Efficiency
Smart switchgear reduces manual inspections and allows remote diagnostics, leading to faster response times and reduced human error.
2. Enhanced Safety
Early detection of overload, arc flash risks, or abnormal temperatures enhances on-site safety, especially in high-voltage environments.
3. Data-Driven Decisions
Real-time analytics help engineers understand load patterns and optimize distribution for efficiency and cost savings.
4. Seamless Scalability
Modular smart systems allow for quick expansion of power infrastructure, particularly useful in growing industrial or smart city projects.
Applications Across Industries
Manufacturing Plants — Monitor energy use per production line
Data Centers — Ensure uninterrupted uptime and cooling load balance
Commercial Buildings — Integrate with BMS (Building Management Systems)
Renewable Energy Projects — Balance grid load from solar or wind sources
Oil & Gas Facilities — Improve safety and compliance through monitoring
What Engineers Need to Know Moving Forward
1. Stay Updated with IEC & IEEE Standards
Smart switchgear must comply with global standards. Engineers need to be familiar with updates related to IEC 62271, IEC 61850, and IEEE C37 series.
2. Learn Communication Protocols
Proficiency in Modbus, DNP3, IEC 61850, and OPC UA is essential to integrating and troubleshooting intelligent systems.
3. Understand Lifecycle Costing
Smart switchgear might have a higher upfront cost but offers significant savings in maintenance, energy efficiency, and downtime over its lifespan.
4. Collaborate with IT Teams
The line between electrical and IT is blurring. Engineers should work closely with cybersecurity and cloud teams for seamless, secure integration.
Conclusion
Smart switchgear is reshaping the way electrical systems are built and managed in 2025. For electrical engineers, embracing this innovation isn’t just an option — it’s a career necessity.
At Blitz Bahrain, we specialize in providing cutting-edge switchgear solutions built for the smart, digital future. Whether you’re an engineer designing the next big project or a facility manager looking to upgrade existing systems, we’re here to power your progress.
#switchgear#panel#manufacturer#bahrain25#electrical supplies#electrical equipment#electrical engineers#electrical
6 notes
·
View notes
Text

Deep Dives into Tech and Digital Growth Strategies
In an era of rapid technological advancements and evolving business landscapes, understanding the nuances of tech-driven strategies is essential for sustained growth. Companies today must leverage cutting-edge technologies and innovative digital growth strategies to stay competitive. This article takes a deep dive into the world of technology and digital strategies, highlighting how businesses can harness them to achieve their full potential.
Tech Innovation: The Catalyst for Business Evolution
Innovation in technology is reshaping industries, from manufacturing and healthcare to retail and financial services. Businesses that embrace tech innovations can unlock new opportunities and create unique competitive advantages.
Automation and AI: Automation tools and artificial intelligence (AI) are driving efficiency, reducing human errors, and freeing up resources for more strategic tasks. Companies that adopt AI-driven decision-making processes gain valuable insights and predictive analytics.
Cloud Computing: Cloud-based solutions offer businesses scalable, cost-effective options for data storage and software deployment. Cloud technologies facilitate remote work, enhance collaboration, and provide data accessibility from any location.
Internet of Things (IoT): IoT is transforming industries by connecting devices and enabling real-time data collection and analysis. Businesses can leverage IoT to monitor operations, optimize workflows, and improve customer experiences.
5G Connectivity: The rollout of 5G networks is enabling faster communication and data transfer. This enhanced connectivity paves the way for innovations in areas like telemedicine, augmented reality, and autonomous vehicles.
Digital Marketing Strategies for Sustainable Growth
Digital marketing is at the heart of modern business strategies. To stand out in a crowded market, businesses must adopt targeted and innovative marketing tactics.
Search Engine Optimization (SEO): SEO is critical for improving online visibility and driving organic traffic. Businesses should focus on creating high-quality content, optimizing for keywords, and building authoritative backlinks to enhance search engine rankings.
Content Marketing: Content is king when it comes to building brand authority and engaging audiences. Businesses should invest in creating informative, relevant content that addresses customer pain points and provides solutions.
Social Media Engagement: Social media platforms are powerful tools for building brand awareness and fostering community engagement. Consistent posting, audience interaction, and strategic advertising can amplify a brand’s reach.
Data-Driven Marketing: Analyzing marketing performance data allows businesses to make informed decisions and refine strategies. By leveraging analytics tools, businesses can identify trends, understand customer behaviors, and optimize campaigns for better results.
Personalization: Today’s consumers expect personalized experiences. Businesses that use data to tailor their offerings and communication to individual preferences are more likely to build lasting relationships with customers.
Cybersecurity: Protecting Digital Assets
As businesses become more reliant on digital technologies, cybersecurity is paramount. Cyber threats can compromise sensitive data, disrupt operations, and damage reputations. To safeguard digital assets, businesses must implement robust cybersecurity measures.
Multi-Layered Security: Implementing multi-layered security protocols ensures that businesses are protected from various attack vectors. This includes firewalls, intrusion detection systems, and endpoint protection.
Data Encryption: Encrypting sensitive data both in transit and at rest protects it from unauthorized access.
Regular Audits: Conducting regular security audits helps identify vulnerabilities and ensures that security measures are up-to-date.
Employee Training: Human error is a common cause of data breaches. Educating employees on cybersecurity best practices can reduce the risk of phishing attacks and other social engineering tactics.
Customer-Centric Tech Solutions
Understanding and prioritizing customer needs is key to business growth. Tech innovations can enhance customer experiences and build long-term loyalty.
Customer Relationship Management (CRM) Systems: CRM systems help businesses manage customer interactions and provide personalized experiences. By analyzing customer data, businesses can tailor their offerings and improve satisfaction.
Chatbots and Virtual Assistants: AI-powered chatbots offer 24/7 customer support, answering queries and resolving issues in real-time. These tools enhance customer service while reducing operational costs.
Omnichannel Experiences: Today’s consumers interact with businesses across multiple channels. Providing a seamless, consistent experience across all touchpoints—whether online, in-store, or on mobile—is essential for customer satisfaction.
Tech Integration for Operational Efficiency
Integrating technology into core business processes can streamline operations, reduce costs, and improve overall efficiency.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate various business functions into a unified platform, improving visibility and coordination across departments.
Project Management Tools: Digital project management platforms enable teams to collaborate, track progress, and meet deadlines efficiently.
Supply Chain Optimization: Advanced technologies like IoT and blockchain can enhance supply chain transparency, improve inventory management, and reduce delays.
Sustainable Growth with Tech Partnerships
Partnering with tech solution providers can accelerate business transformation and growth. Collaborating with experts allows businesses to access specialized knowledge and cutting-edge technologies without investing heavily in in-house resources.
Scalability: Tech partnerships enable businesses to scale operations as needed, adapting to market demands without significant disruptions.
Innovation: Partnering with tech innovators ensures that businesses stay ahead of industry trends and adopt new technologies as they emerge.
Looking Ahead: Future Trends in Tech and Digital Growth
The tech landscape is constantly evolving, and businesses must stay agile to remain competitive. Emerging trends like artificial intelligence, quantum computing, and edge computing are set to redefine industries. By staying informed and embracing change, businesses can position themselves for long-term success.
Conclusion
Tech4Biz Solutions is committed to empowering businesses with innovative tech solutions and digital growth strategies. Whether it’s leveraging advanced technologies, optimizing marketing efforts, or enhancing customer experiences, Tech4Biz helps businesses unlock new possibilities. By diving deep into the world of tech and digital strategies, companies can fuel growth, drive innovation, and stay ahead of the curve in an ever-changing business landscape. Visit Tech4Biz Solutions to learn more about how we can help transform your business.
5 notes
·
View notes
Text
A Comprehensive Guide to Navigating the Underground Sex Trade
Disclaimer: This narrative is a raw, uncensored exploration of the hidden world, designed to empower and safeguard women who choose to challenge societal norms and authority. It's a non-fictional, strategic guide that delves deep into the intricacies of survival and success in this illicit domain.

Chapter 1: Deciphering the Legal Maze
Unveiling the Legal Landscape: Before embarking on this journey, it's crucial to understand the laws that you seek to defy. Prostitution laws vary globally, from outright prohibition to decriminalization and even legalization in some jurisdictions. Research the specific statutes in your intended area of operation. Are sex workers, pimps, clients, or all three criminalized? This knowledge will shape your tactics.
Analyzing Enforcement Patterns: Law enforcement agencies differ in their approach to prostitution. Study the local police's tactics. Are they actively conducting sting operations and raids, or do they maintain a more passive presence? Identifying hot spots for police activity will help you steer clear of potential traps. Stay updated on the latest enforcement trends through discreet channels and underground networks.
Chapter 2: Choosing Your Path

Street Trade: Risks and Rewards: Streetwalking is a high-risk, high-reward strategy. If you choose this path, scout for less-traveled, dimly lit streets, avoiding popular red-light districts. Develop a keen sense of awareness, learning to identify potential clients and undercover police. Discretion is paramount; blend into the shadows and trust your instincts for survival. Traveling in small groups can increase safety but also increases potential to draw attention.
Brothels and Hidden Establishments: Operating from an established location offers a sense of security. Seek out illegal brothels or massage parlors that operate under the radar. These places often have connections and systems in place to ensure anonymity. However, be cautious, as they might be under surveillance or outright honeypots. Use aliases, and never disclose personal details, ensuring your identity remains protected.
The Escort Route: Disguise as Legitimacy: Becoming an escort allows for a more sophisticated facade. Create anonymous profiles on encrypted platforms catering to clients seeking discretion. Establish a reputation for yourself, but always prioritize safety. Thoroughly vet clients, and consider employing a trusted intermediary to arrange meetings, ensuring you remain one step removed from potential danger.
Chapter 3: Safeguarding Your Identity and Freedom

Anonymity as Armor: Protecting your true identity is a cornerstone of survival. Create and maintain a separate persona for this world. Never share personal information, and avoid carrying documents that can expose your real identity. Use encrypted communication tools, and frequently change your contact methods to prevent tracking.
Screening Clients: A Vital Practice: Your safety hinges on careful client selection. Always meet in public places for the initial encounter, and trust your instincts. Implement a rigorous screening process, including references from other sex workers or verification through discreet, trusted online communities. Be vigilant for signs of law enforcement or potential threats. Ask for an up to date STD test for your safety.
Communication Tactics: Encryption is your ally. Utilize secure messaging apps like signal and temporary phone or anonymous numbers to communicate with clients and colleagues. Regularly update your online presence, erasing any digital footprints that could compromise your identity. Maintain a network of trusted contacts, but exercise caution in sharing information, even within this circle.
Chapter 4: Evading Authority and Surveillance

Mastering Disguise: Your appearance is a powerful tool. Learn the art of disguise, adapting your look to blend into different environments. When not working, shed your trade persona, becoming a chameleon in plain sight. Invest in makeup, wigs, and accessories that aid in transforming your appearance, making it harder for anyone to recognize you.
Knowing Your Legal Rights: Understand your legal rights during police interactions. You have the right to remain silent, and sometimes, silence is your most potent defense. Familiarize yourself with local search and seizure laws to protect yourself from unlawful intrusions. Remember, the less you reveal, the more power you hold.
Confronting Raids and Arrest: Prepare for the worst-case scenario. If faced with a police raid, maintain your composure. Do not resist arrest, as it may escalate the situation. Document any rights violations and seek legal counsel experienced in defending sex workers' rights. Remember, knowledge of your rights is a powerful tool in navigating the justice system.
Chapter 5: Financial Sovereignty

Cash and Cryptocurrency: In the underground economy, cash is king. Set up multiple anonymous bank accounts if possible to deposit your earnings. Consider cryptocurrencies for added financial secrecy, but be careful, Cryptocurrency like Bitcoin isn't anonymous by default. While money laundering is illegal, exploring techniques to obscure the source of your income can reduce the risk of detection.
Evasive Financial Tactics: Tax evasion is a necessary skill. Maintain a low financial profile to avoid scrutiny from tax authorities. Structure your finances to minimize paper trails, and consider investing in assets that are difficult to trace, such as precious metals, cryptocurrencies or both.
Building a Safety Net: Prioritize saving a portion of your earnings. This nest egg will provide financial security, allowing you to exit the trade if needed. It also ensures a backup in case of legal complications, where you might need to pay for legal counsel or bail.
Chapter 6: Community and Self-Preservation

Building a Support Network: Navigating this world can be isolating. Cultivate a small, trusted circle of colleagues or friends who understand your lifestyle. Mutual support and information sharing can enhance your safety and provide emotional respite.
Self-Defense and Security: Invest in self-defense training to protect yourself physically. Learn to identify and handle dangerous situations, and always prioritize your safety above all else. Carry discreet self-defense tools, and remain vigilant, especially in unfamiliar territories.
Mental Resilience: Engaging in this profession can take a toll on your mental health. Develop coping mechanisms and seek support to process the emotional challenges. Remember, your well-being is paramount, and self-care is an act of resistance against a society that seeks to control and oppress.
Conclusion: The Underground Odyssey
Embarking on a journey into the underground sex trade is a bold defiance of societal norms and authority. This guide has unveiled strategies to minimize risks, but it's essential to acknowledge the inherent perils.
Weird Guides presents this information to empower individuals, especially women, to make informed choices and protect themselves from abuse and overzealous government intrusion. The choice to enter this realm is yours alone, but with knowledge and caution, you can navigate the shadows with resilience and autonomy.
In the dance between breaking free and staying hidden, remember that every step carries consequences. Stay informed, stay vigilant, and always trust your instincts in this complex and clandestine world.
#sex worker#sex work is work#sex work is real work#sex worker rights#adult entertainment#adult entertainers#breaking the law#feminism#fuck the patriarchy#femisnism
2 notes
·
View notes
Text
Role of ethical hackers in the fight against ransomware attacks

Ransomware attacks are now one of the most damaging cyber threats as they target not only businesses, healthcare systems, and educational institutions but also governments. These types of attacks lock up critical data and demand that a ransom be paid to decrypt it, leaving massive financial and reputational damages in their wake. In this high-stakes game of cyber warfare, the role of the ethical hacker has come into the picture as a vital player protecting organizations from ransomware attacks. Here's how these cyber guardians are making a difference.
What Are Ethical Hackers?
Ethical hackers are usually called "white-hat" hackers. These are cybersecurity experts who make use of their expertise to discover weaknesses in systems, networks, and applications before they can be exploited by cybercriminals. In contrast to cybercriminals, ethical hackers collaborate with organizations to build stronger defenses and achieve security compliance.
If you wish to become a part of this exclusive club of cyber defenders, you should take a course in cyber security and ethical hacking. This type of course will help you learn to think like a hacker so you can think ahead and eliminate possible threats.
Ransomware Threat Landscape
The attacks by ransomware have been very sophisticated. From using advanced phishing to exploiting zero-day vulnerabilities and even using artificial intelligence to target their victims, ransomware attackers have developed into highly skilled actors. In addition, Ransomware-as-a-Service (RaaS) platforms have further democratized these attacks, even making them possible for the less technically skilled cybercriminals.
Recent estimates suggest ransomware damages are expected to go above $30 billion annually by 2025. This growing threat requires aggressive cybersecurity measures that incorporate the input of ethical hackers.
How Ethical Hackers Fight Ransomware
Proactive Vulnerability Scanning Ethical hackers carry out vulnerability scans to scan the organization's infrastructure for vulnerable spots. Using a simulated ransomware attack, they can reveal how exposed an organization is to risk and implement relevant remediation efforts.
Penetration Testing Penetration testing is an attempt by ethical hackers to breach the defenses of an organization in a controlled environment. It shows security gaps and tests the effectiveness of existing measures.
Phishing Simulations and Training Since phishing is the most common vector for ransomware attacks, ethical hackers simulate phishing campaigns. These exercises train employees to recognize and respond to malicious emails, thus reducing the risk of a successful attack.
Incident Response and Recovery Incident response at ransomware strikes includes the input of ethical hackers to help contain an attack, understand a breach, and assist in retrieving encrypted files without paying any ransom.
Monitoring and Threat Intelligence Ethical hackers keep themselves aware of new emerging threats and the ransomware trend. The organizations would not miss being on their toes if ethical hackers help them build on new defensive systems and patches in place soon enough.
Becoming an Ethical Hacker
The demand for ethical hackers is rapidly increasing, considering the recognition that organizations from any industry require proactive cybersecurity. It is an integrated cyber security and ethical hacking course that would teach you how to be one. From penetration testing to advanced threat detection, courses provide you with hands-on exposure to real scenarios.
Conclusion
Ethical hackers are the unsung heroes in the fight against ransomware. Their proactive approach, technical expertise, and unwavering commitment to cybersecurity make them indispensable in safeguarding our digital world. If you’re passionate about technology and problem-solving, a career in ethical hacking could not only be rewarding but also instrumental in making the internet a safer place.
Enroll in a cyber security and ethical hacking course today and become part of the frontline defense against ransomware attacks. The world needs more defenders, and now is the starting point for that journey.
2 notes
·
View notes
Text

Emerging Trends Shaping the Future of White-Label Crypto Exchange Development
The cryptocurrency market has seen exponential growth over the years, and as demand for seamless and feature-rich trading platforms rises, white-label crypto exchange development has become a game-changing solution for businesses. A white-label crypto exchange allows entrepreneurs to quickly launch a customizable trading platform, eliminating the need for extensive development time and resources.
As the crypto landscape evolves, so do the expectations for white-label solutions. In this blog, we’ll explore the future trends shaping white-label crypto exchange development, showcasing how businesses can stay competitive and meet the ever-changing demands of traders.
1. Increased Focus on Decentralized Exchange Features
Decentralized exchanges (DEXs) are becoming increasingly popular due to their security and transparency. As a result, many white-label solutions are integrating DEX functionalities into their offerings.
Key Trends:
Hybrid Models: Combining the security of DEXs with the liquidity of centralized exchanges (CEXs).
Non-Custodial Wallets: Allowing users to trade directly from their wallets without intermediaries.
Smart Contract Integration: Automating trading processes and enhancing security.
Why It Matters:
DEX-like features in white-label solutions cater to the growing demand for privacy and decentralization, attracting a broader user base.
2. Multi-Asset Support and Tokenization
With the rise of tokenized assets and diverse cryptocurrencies, future white-label exchanges will focus on supporting a wide range of assets.
What to Expect:
Support for tokenized stocks, commodities, and real estate.
Integration of emerging blockchain networks like Solana, Avalanche, and Polkadot.
Cross-chain compatibility for seamless trading across multiple blockchain ecosystems.
Impact:
Businesses that offer multi-asset trading options will attract institutional and retail investors seeking diverse investment opportunities.
3. Advanced Security Measures
Security remains a top concern in the crypto industry. Future white-label crypto exchanges will incorporate state-of-the-art security measures to protect user funds and data.
Innovative Security Features:
Multi-Signature Wallets: Ensuring transactions require multiple approvals.
Cold Storage Solutions: Safeguarding the majority of funds offline.
AI-Powered Fraud Detection: Identifying and mitigating suspicious activities in real-time.
End-to-End Encryption: Securing user data and communication.
Why It’s Important:
Enhanced security builds trust, which is crucial for attracting and retaining users in the competitive crypto exchange market.
4. Customizable User Experiences (UX/UI)
As competition grows, user experience (UX) will become a key differentiator. White-label exchanges will prioritize customizable and intuitive interfaces.
Future Developments in UX/UI:
Personalized Dashboards: Allowing users to customize their trading view.
Simplified Onboarding: Streamlining the KYC process for faster registration.
Mobile-First Design: Optimizing platforms for seamless use on smartphones.
Dark Mode and Accessibility Features: Catering to diverse user preferences.
Result:
User-friendly platforms enhance engagement and attract a wider audience, including beginners entering the crypto space.
5. Integration of DeFi Features
Decentralized finance (DeFi) is one of the fastest-growing sectors in the crypto industry. Future white-label solutions will integrate DeFi functionalities to meet user demands for innovative financial services.
Popular DeFi Features:
Staking and Yield Farming: Enabling users to earn passive income.
Lending and Borrowing: Providing decentralized financial services.
Liquidity Pools: Allowing users to earn rewards by providing liquidity.
Why It Matters:
Incorporating DeFi features enhances platform functionality and attracts users looking for diverse earning opportunities.
6. AI and Machine Learning Integration
Artificial intelligence (AI) and machine learning (ML) are revolutionizing the way crypto exchanges operate. Future white-label exchanges will harness these technologies for automation and efficiency.
AI-Powered Features:
Predictive Analytics: Helping users make data-driven trading decisions.
Automated Trading Bots: Enabling high-frequency and algorithmic trading.
Fraud Detection: Identifying suspicious activities and enhancing security.
Outcome:
AI integration improves platform performance and user satisfaction, giving businesses a competitive edge.
7. Compliance and Regulatory Readiness
With governments worldwide tightening regulations on cryptocurrencies, compliance will be a critical factor for future exchanges.
What to Expect:
Automated KYC/AML Processes: Using AI to verify user identities and prevent money laundering.
Transparent Reporting: Providing real-time audit trails for regulators.
Global Regulatory Support: Adapting platforms to comply with regional laws.
Impact:
Regulatory-compliant exchanges inspire confidence among users and attract institutional investors.
8. Gamification in Trading
Gamification is emerging as a strategy to enhance user engagement on trading platforms. Future white-label crypto exchanges will incorporate interactive elements to make trading more engaging.
Gamification Features:
Leaderboards: Highlighting top traders and rewarding performance.
Achievements and Badges: Encouraging users to reach milestones.
Demo Trading: Offering virtual trading environments for beginners.
Why It’s Effective:
Gamification boosts user retention and makes trading enjoyable, particularly for younger demographics.
9. White-Label NFT Marketplaces
The rise of non-fungible tokens (NFTs) has created new opportunities for crypto exchanges. White-label platforms will increasingly support NFT trading and minting.
Key Features:
NFT Minting Tools: Allowing users to create and sell digital assets.
Integrated Marketplaces: Enabling seamless buying and selling of NFTs.
Royalty Management: Automating creator royalties using smart contracts.
Impact:
Businesses that offer NFT capabilities can tap into a growing market and attract creators and collectors alike.
10. Scalability and Performance Optimization
As the user base for crypto exchanges grows, scalability and performance will remain top priorities for white-label solutions.
Enhancements:
Layer-2 Scaling: Using solutions like Polygon for faster and cheaper transactions.
Cloud-Based Infrastructure: Ensuring platform reliability during traffic spikes.
Low Latency Trading: Enabling high-speed transactions for professional traders.
Result:
Scalable platforms can handle larger user bases and higher trading volumes, ensuring a seamless experience for all users.
Why Partner with Professional White-Label Crypto Exchange Development Services?
To stay competitive in the evolving crypto market, partnering with an experienced white-label crypto exchange development company is essential.
Key Benefits:
Custom Solutions: Tailored platforms with unique branding and features.
Quick Launch: Faster time-to-market compared to building from scratch.
Security Integration: Advanced measures to safeguard user funds and data.
Ongoing Support: Regular updates and technical assistance to ensure smooth operations.
Conclusion
The future of white-label crypto exchange development lies in innovation, security, and user-centric features. From integrating DeFi functionalities to offering multi-asset support and gamification, the next generation of white-label solutions will empower businesses to thrive in the competitive crypto space.
By leveraging the latest trends and partnering with professional development services, businesses can launch cutting-edge platforms that attract users, drive engagement, and generate sustainable revenue.
Ready to build your own white-label crypto exchange? The future is now—embrace innovation!
#crypto exchange platform development company#crypto exchange development company#cryptocurrency exchange development service#crypto exchange platform development#white label crypto exchange development#cryptocurrencyexchange#cryptoexchange
3 notes
·
View notes
Text
Understanding Privacy Breaches in India: A Growing Concern
Privacy breaches are becoming a prevalent yet gravely worrisome problem in today's increasingly digital world, especially in India, where a plethora of new cyber threats have been brought about by fast digitization. Data breaches are more dangerous than ever as more people rely on digital platforms for banking, retail, communication, and even government functions. Protecting personal information is essential for both individuals and businesses and not doing so can have dire repercussions. This blog explores the definition of privacy breaches, their effects, and self-defence measures. Any unauthorized access, sharing, or theft of personal information constitutes a privacy breach. This may occur as a result of a deliberate hacking attempt or an unintentional disclosure. Privacy breaches are frequently more personal in nature, focusing on sensitive information like your name, financial information, or private chats, in contrast to data breaches, which usually involve the exposure of vast amounts of data. Millions of people have been impacted by these breaches, which have increased in frequency in India, where internet penetration is rising quickly.
Data leaks are among the most prevalent kinds of privacy violations. When private information is unintentionally made public by inadequate security measures, it is referred to as a data leak. These breaches can happen when businesses neglect to encrypt private information, making it open to illegal access. For instance, millions of people's names, addresses, and identification numbers were made public in 2021 due to a huge database leak in India, raising serious concerns about fraud and identity theft. Unauthorized access is another frequent way that privacy is violated. Cybercriminals obtain unauthorized access to networks or accounts using a variety of methods. For example, phishing is a popular technique where attackers deceive victims into disclosing personal information or login passwords. The attacker can access private accounts, steal information, or even perpetrate financial fraud once they have this data. Phishing assaults have increased in India, where the perpetrators frequently impersonate reputable organizations, such as banks or government offices, in order to trick their victims. In India, identity theft is yet another common privacy violation. To impersonate someone, criminals take their personal information, including their Aadhaar number. They can start phony bank accounts, commit crimes, or make purchases using the victim's name using this stolen identity. This kind of privacy violation has become especially harmful to the victims, both financially and emotionally, as a result of the increased reliance on digital identification and financial systems.
Another important factor in privacy violations is social media. By excessively disclosing personal information on social media sites like Facebook, Instagram, and Twitter, many Indians unwittingly jeopardize their privacy. Social media breaches happen when hackers make use of publicly accessible information to obtain additional private information or coerce users into disclosing even more private information. Alarming facts support the growing trend of privacy breaches in India. Over 1.16 million cybercrimes were reported in India in 2020 alone, a large percentage of which entailed privacy breaches, according to recent data. Victims may suffer terrible financial and psychological costs, and the consequences are frequently permanent. Since more personal information is being kept online than ever before, there is a greater chance of breaches, which makes cybersecurity a critical concern for both individuals and companies. The effects of privacy violations are extensive. Individuals may experience financial loss, reputational harm, or identity theft as a result of data breaches. Knowing that criminals have access to their personal information frequently causes victims to feel anxious or distressed. The repercussions are just as bad for corporations. Legal issues, significant fines, and a decline in customer trust might result from a privacy violation. After a major breach, some businesses may be compelled to close since the harm to their brand is irreversible.
Preventive actions are crucial in the fight against privacy violations. People should exercise caution when using the internet by creating strong, one-of-a-kind passwords for every account, turning on two-factor authentication, and being careful about what they post on social media. In order to guard against vulnerabilities, it's also essential to update programs and software often. Businesses need to make investments in robust cybersecurity procedures, like encrypting confidential information, carrying out frequent security audits, and teaching staff members how to spot phishing scams.
In conclusion, privacy violations are becoming a bigger issue in India that impacts both people and businesses. The threats of cybercrimes will only rise as long as we continue to rely on digital platforms. We can reduce the possibility of falling victim to a privacy breach by being aware of the risks and adopting preventative measures to safeguard personal data. Keep yourself informed, remain safe, and safeguard your online privacy.
2 notes
·
View notes
Text
Ransomware Attacks Target VMware ESXi Infrastructure Following Interesting Pattern

Cybersecurity firm Sygnia has shed light on a concerning trend where ransomware attacks targeting VMware ESXi infrastructure follow a well-established pattern, regardless of the specific file-encrypting malware deployed. According to the Israeli company's incident response efforts involving various ransomware families, these attacks adhere to a similar sequence of actions.
The Attack Sequence
- Initial access is obtained through phishing attacks, malicious file downloads, or exploitation of known vulnerabilities in internet-facing assets. - Attackers escalate their privileges to obtain credentials for ESXi hosts or vCenter using brute-force attacks or other methods. - Access to the virtualization infrastructure is validated, and the ransomware is deployed. - Backup systems are deleted, encrypted, or passwords are changed to complicate recovery efforts. - Data is exfiltrated to external locations such as Mega.io, Dropbox, or attacker-controlled hosting services. - The ransomware initiates execution and encrypts the "/vmfs/volumes" folder of the ESXi filesystem. - The ransomware propagates to non-virtualized servers and workstations, widening the scope of the attack.

Mitigation Strategies
To mitigate the risks posed by such threats, organizations are advised to implement the following measures: - Ensure adequate monitoring and logging are in place - Create robust backup mechanisms - Enforce strong authentication measures - Harden the environment - Implement network restrictions to prevent lateral movement
Malvertising Campaign Distributing Trojanized Installers
In a related development, cybersecurity company Rapid7 has warned of an ongoing campaign since early March 2024 that employs malicious ads on commonly used search engines to distribute infected installers for WinSCP and PuTTY via typosquatted domains. These counterfeit installers act as a conduit to drop the Sliver post-exploitation toolkit, which is then used to deliver more payloads, including a Cobalt Strike Beacon leveraged for ransomware deployment. This activity shares tactical overlaps with prior BlackCat ransomware attacks that have used malvertising as an initial access vector, disproportionately affecting members of IT teams who are most likely to download the infected files.
New Ransomware Families and Global Trends
The cybersecurity landscape has witnessed the emergence of new ransomware families like Beast, MorLock, Synapse, and Trinity. The MorLock group has extensively targeted Russian companies, encrypting files without first exfiltrating them and demanding substantial ransoms. According to NCC Group's data, global ransomware attacks in April 2024 registered a 15% decline from the previous month, with LockBit's reign as the top threat actor ending in the aftermath of a sweeping law enforcement takedown earlier this year. The turbulence in the ransomware scene has been complemented by cyber criminals advertising hidden Virtual Network Computing (hVNC) and remote access services like Pandora and TMChecker, which could be utilized for data exfiltration, deploying additional malware, and facilitating ransomware attacks. Read the full article
4 notes
·
View notes